Securing Access to your Cloud Resources

Securing Access to your Cloud Resources We all know about the amazing things we can build in cloud environments – I bang on about it often enough! But what’s the best way to administrate your environment once it exists? What is safe to leave open to the Internet and what should be shrouded in a […]
Internet of Things – IoT – Explained

Internet of Things – IoT – Explained We love to bust jargot wherever we can, so this week, we’re talking about the Internet of Things – IoT. IoT is thrown around all over, and you’re expected to just understand what it is, and how it all works. We’re here to help! What is IoT? We […]
What is a VPN?

What is a VPN? Virtual Private Networks, or VPNs are all the rage at the moment. Every other video I watch on YouTube includes an advertisment for one Scandinavian VPN solution or another. But what is a VPN, and why might you want one? Virtual Private Network – VPN Virtual The V is for Virtual. […]
Why You Need Good Passwords

Why You Need Good Passwords In last week’s blog post, we showed you how to check if your online accounts have been compromised. We’re all told that we should change our passwords regularly, right? That is even more important if one of your online identities has been leaked. So this week, we’re answering the question […]
Security Precautions as a Managed Service Provider

Security Precautions as a Managed Service Provider We talk about security an awful lot here at Beaty Consultancy. We’re a little bit obsessed with it. But isn’t that a good thing? If you’re going to trust us with access to all your data, and data belonging to your clients, shouldn’t we be security draft? I […]
Here’s Why You Need a Web Application Firewall

Here’s Why You Need a Web Application Firewall If you’re reading this, the chances are that you run a web application. What do we mean by a web application? Now that websites are so responsive and feature-rich, we’re basically talking about everything on the Internet! WordPress? Web application. Joomla? Moodle? Drupal? Yep, they’re all web […]
Managing your cloud account logins
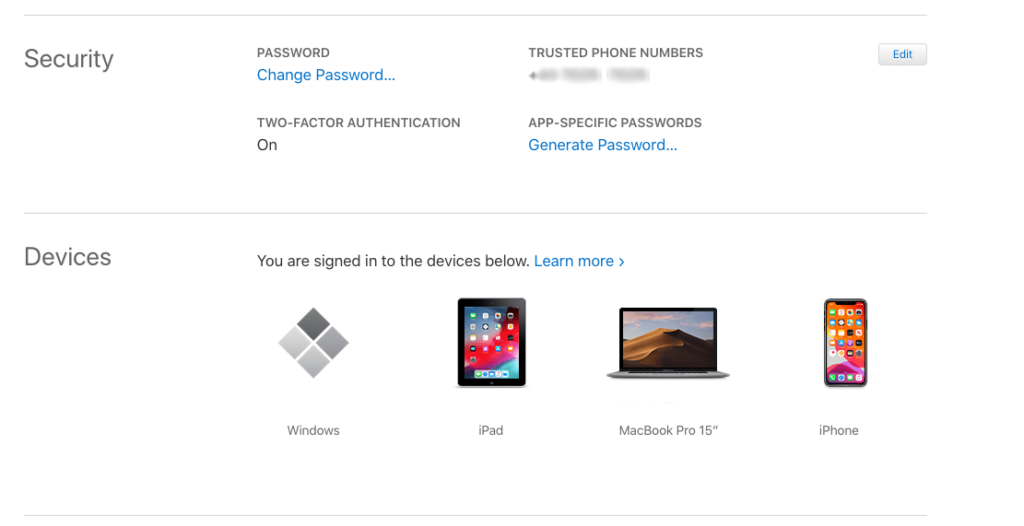
Managing your cloud account logins We’ve spoken about what cloud is before, so you already know that you’re using cloud technologies everywhere. But when was that last time you checked where you’re signed in to all of those cloud accounts from? When you traded your old mobile, tablet or laptop in, are you sure you […]
Protecting your business from Ransomware

Protecting your business from Ransomware First thing’s first – what is Ransomware? Ransomware is when your data is maliciously encrypted, and a ransom is demanded in order for you to get they keys to unencrypt your data. While your data is in it’s encrypted state, you can’t use it. It might as well have been […]
Thanks for the downtime

Thanks for the downtime It’s Saturday morning, early. I’m feeling super productive today, so I’ve already walked the dog, put last night’s dishes away, fed the Guinea pigs, and made myself a huge gingerbread latte. Time to get down to some serious work before some fun stuff I have planned with friends later. I open […]


